Two Factor Authentication (TFA) - Beyond Passwords
We all know that good passwords are complicated, should be different for every use and change frequently. We also know how hard that is to implement, enforce and track. So what do we do about this? Two factor authentication (TFA), which combines your username and password with something you have (tokens) and something you are (biometrics) comes to the rescue. One time passwords (OTP), which can be implemented as two factor authentication, are a very good, low-cost option that might be part of your existing firewall already in place. Let’s take a closer look.
Something You Have (Tokens)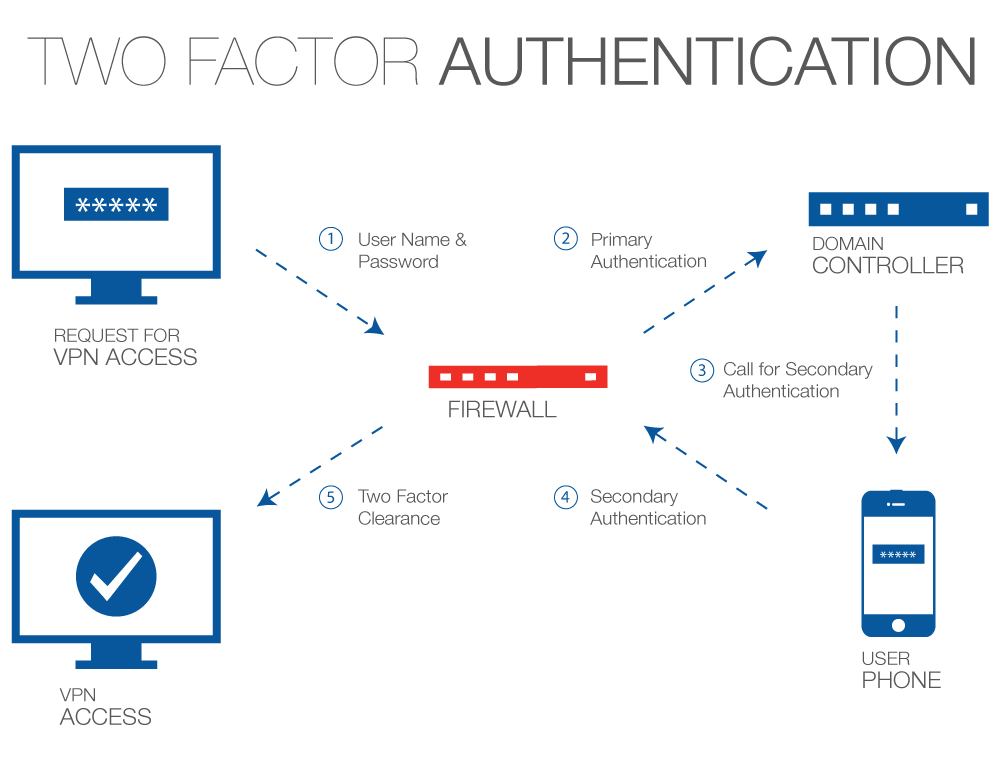
The most common type of two-factor authentication combines your username and password with a “token” device that provides a six- or eight-digit alpha or alphanumeric code to provide you access. These codes change frequently (typically every minute), making them quite secure. You may already use these to access banking or brokerage account(s), both very common use scenarios. Adding token-based TFA to protect remote access is relatively easy and cheap to do and is very secure. The tokens are reliable but you have to remember to have them with you!
Something You Are (Biometrics)
Biometrics technology has migrated from the movies, to everyday use over the past decade. Biometrics examples include fingerprint sensors (laptops and Smartphones usually), retinal scanners (most often used to protect physical access to controlled areas) and facial recognition (Smartphones again). Biometric technology tends to be harder and more expensive to implement, and false negatives are still a bit of a problem. Costs to implement can also be higher than token-based two factor authentication, but you cannot forget to carry your finger with you!
On the Cheap – One Time Passwords
One Time Passwords (OTP) also known as Smartphone two factor authentication is very simple and straightforward. You try to access your network remotely and in addition to your username/password combination you are immediately sent (by email or text) a single-use password that you must add to your standard credentials in order to gain access. OTPs are most commonly used to protect remote connections, but do have other uses as well. The best news of all is that OTP is built into the best new Firewalls and can be implemented in less than an hour!
But Really . . . Why Do I Need It?
So now that you understand your options, you may still wonder . . . why do I need two-factor authentication? Let’s review three things. First, passwords are very hard to make secure, keep secure and manage. Second, your employees will almost always find a way around your security policies, including the sharing of passwords, using overly simple passwords, or simply by writing passwords on notes attached to their monitors. With two factor authentication you add that extra layer of security, so that even with a username/password, without that second factor (token or biometrics) you are not getting in.
Finally, take a moment to consider the following scenario. You have to lay off someone one day, someone pretty computer savvy. They leave and you shut down their user account, but they know how things work there and they know other user passwords. If you are not using two-factor authentication for that user,you have to change EVERY password in the company to lock that person out. Two factor authentication not only adds a layer of protection to your network for your staff, it provides you the control you need to quickly and effectively lock things down if that staff changes.


